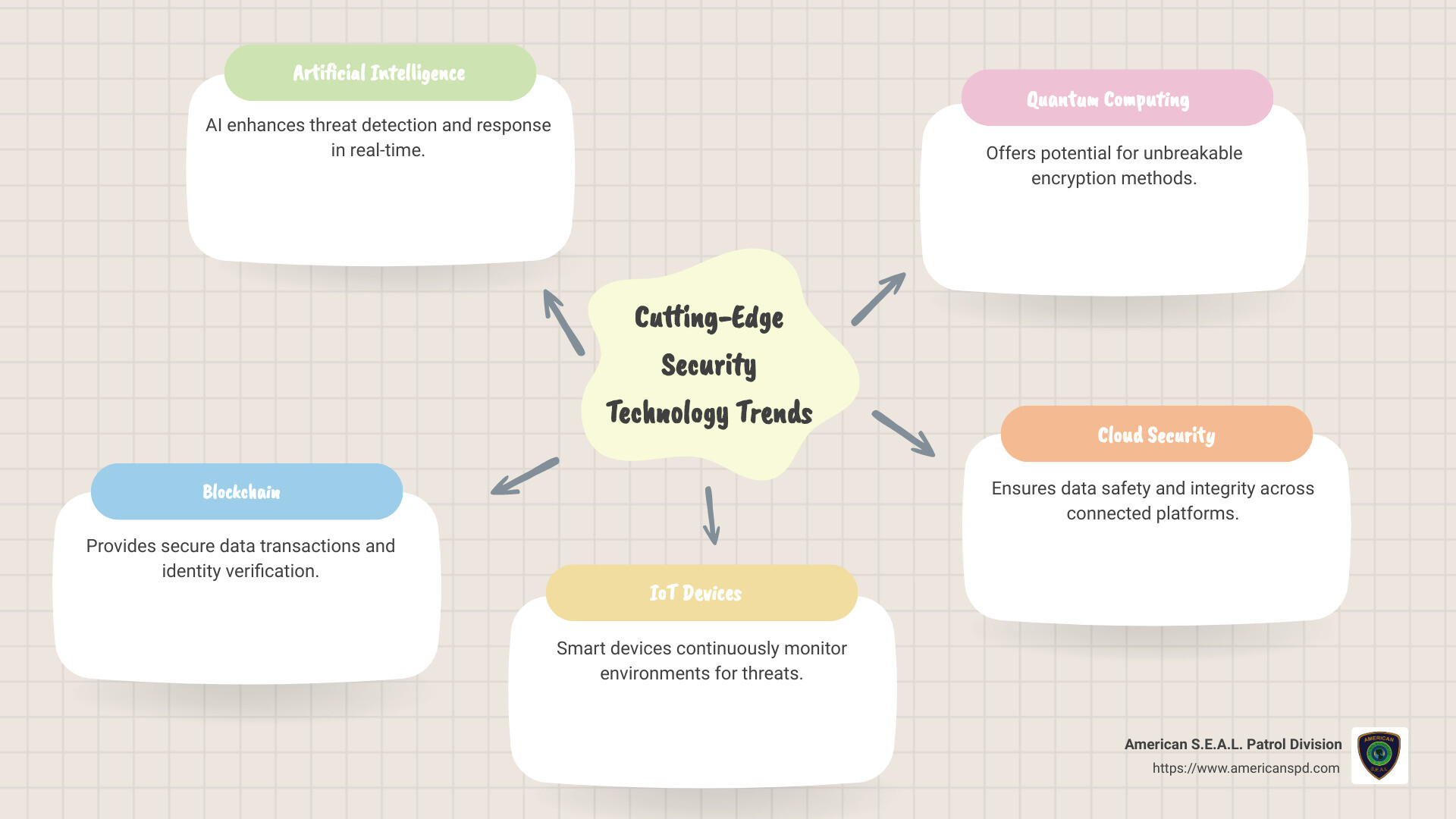
Cutting-edge security technology is changing how we protect our digital and physical spaces. In today’s world, security needs are evolving rapidly:
-
Cybersecurity Importance: In a digital-first era, cybersecurity has become essential. It’s not just about protecting data; it’s about ensuring day-to-day operations run smoothly without disruptions.
-
Digital Threats: As technology advances, so do digital threats. Hackers and cybercriminals are constantly finding new ways to breach systems, making robust security measures a priority.
-
Technology Advancements: Emerging technologies such as artificial intelligence, blockchain, and cloud computing are revolutionizing security solutions. These innovations help in detecting threats faster and securing sensitive information more effectively.
Technology-driven security systems act as guardians of our modern world. As challenges continue to grow, keeping up with these advancements ensures safety and peace of mind, especially for property managers like Sarah Thompson, who values comprehensive solutions for protecting her properties.
Cutting-Edge Security Technology in Cybersecurity
Artificial Intelligence (AI) has become a cornerstone of modern cybersecurity. Imagine a world where security systems learn and adapt on their own. That’s what AI can do. It processes vast amounts of data to identify patterns and detect threats almost instantly. This means quicker responses to cyberattacks and improved protection for sensitive information. AI-driven solutions are like having a vigilant guard who never sleeps.
Robotics is another exciting area. Picture robots patrolling premises, ensuring safety and security. These machines can work alongside human guards, handling routine tasks and freeing up personnel for more complex duties. Robotics improves efficiency and can operate in environments that might be hazardous for humans.
Blockchain technology offers a way to secure data. Known for its use in cryptocurrencies, blockchain is also invaluable in cybersecurity. It creates a tamper-proof record of transactions, making it extremely difficult for hackers to alter data. This transparency and security are critical in protecting digital assets.
IoT Devices (Internet of Things) connect everyday objects to the internet, creating smart environments. While they offer convenience, they also introduce new security challenges. Protecting IoT devices from cyber threats is crucial, as a breach could compromise entire networks. Security solutions are being developed to safeguard these devices, ensuring they remain a benefit rather than a risk.
Quantum Computing is on the horizon, promising to revolutionize data processing. Its immense computing power could potentially break current encryption methods, but it also offers the possibility of creating unbreakable security protocols. As quantum technology evolves, develop security measures that can harness its power safely.
These cutting-edge security technologies are reshaping the cybersecurity landscape. By staying informed and adopting these innovations, organizations can better protect their digital assets and ensure a secure future.
Advanced Surveillance and Monitoring Systems
Advanced surveillance and monitoring systems are essential for ensuring security around the clock. These systems provide 24/7 protection, allowing businesses and individuals to monitor their premises at all times. This constant vigilance is crucial in deterring potential threats and quickly addressing any incidents that may arise.
One of the key components of these systems is the use of surveillance cameras. These cameras are strategically placed to cover critical areas, providing comprehensive visual coverage. The latest models offer high-resolution imaging and advanced features like motion detection and night vision, ensuring clear visibility in various conditions.
Another significant advancement is remote viewing access. This feature allows users to monitor their security feeds from anywhere in the world using a smartphone, tablet, or computer. With remote access, you can check on your property in real-time, receive alerts about suspicious activities, and even review recorded footage—all from the convenience of your device. This flexibility means that you never have to be physically present to ensure your property is secure.
The integration of cutting-edge security technology in these systems improves their effectiveness. For instance, AI-driven analytics can automatically identify unusual patterns or behaviors captured by the cameras, alerting security personnel to potential threats. This reduces the time needed to respond to incidents and improves overall security management.
By adopting these advanced surveillance and monitoring systems, businesses and homeowners can achieve peace of mind knowing that their properties are under constant watch. This proactive approach to security not only protects physical assets but also safeguards the well-being of people within these environments.
The Role of Artificial Intelligence in Security
Artificial Intelligence (AI) is changing how we protect our digital and physical spaces. Its ability to process vast amounts of data quickly makes it an invaluable tool for threat detection.
AI-driven solutions analyze data in real-time to find patterns and anomalies. This means they can spot potential threats that might go unnoticed by human eyes. For example, AI can identify unusual login activities or detect malware before it causes harm. This proactive approach helps to stop attacks before they escalate.
One of the most exciting aspects of AI in security is its automated response capabilities. AI systems can automatically take action when they detect a threat. This might include isolating affected systems, alerting security teams, or even blocking suspicious activities. By automating these responses, organizations can react faster, reducing the risk of damage.
The use of AI in security isn’t just about speed. It’s also about accuracy. AI can continuously learn from new data, improving its threat detection abilities over time. This means it gets better at recognizing both old and new threats.
AI’s role in security is growing rapidly. As cyber threats become more sophisticated, AI provides a way to stay ahead. By integrating AI into their security strategies, organizations can improve their defenses and protect their assets more effectively. This makes AI not just a tool, but a critical partner in the fight against cybercrime.
Zero Trust Security Model
The Zero Trust Security Model is a game-changer in cybersecurity. It flips the traditional idea of trust on its head with a simple mantra: never trust, always verify.
This model assumes that threats can come from anywhere—inside or outside the network. So, it requires continuous authentication and verification for every user and device trying to access the network. No one gets a free pass.
Imagine a secure office building. In the old days, if you had a key card, you could roam freely. But with Zero Trust, you need to show your credentials at every door. It’s like having security guards at every entrance, always checking if you should be there.
Continuous authentication means that even after you’re inside, the system keeps checking if you’re still who you say you are. This might involve re-entering passwords, using biometrics, or confirming your identity through your phone. It’s like having a security badge that needs constant renewal.
This approach drastically reduces the risk of a data breach. Even if a hacker gets in, they can’t move around freely. They face barriers at every turn, making it much harder to cause damage.
Major players like Google Cloud and Microsoft Azure are embracing this model, integrating it into their services to offer tighter security. As digital threats grow, the Zero Trust Security Model becomes not just smart, but essential. It offers a robust framework to protect sensitive data and keep networks safe.
By implementing Zero Trust, organizations can better safeguard their digital assets, ensuring that their security measures are as resilient as possible.
Cloud Security and Connectivity
Cloud Security and Connectivity
Cloud security is more important than ever. As businesses move their operations to the cloud, they need to ensure their data is safe and accessible. That’s where cloud native security comes in.
Cloud native security means building security measures directly into cloud services. This approach is like having a security system designed specifically for your home, rather than a one-size-fits-all solution. It ensures that the security measures are custom to the unique environment of the cloud, providing robust protection for your data.
One of the key technologies enhancing cloud connectivity and security is SD-WAN (Software-Defined Wide Area Network). SD-WAN allows businesses to connect their offices and branches securely over the internet. It’s like having a private highway for your data, ensuring it travels safely and efficiently. This technology not only improves connectivity but also reduces the risk of data breaches by creating a secure network for data transfer.
Another important concept in cloud security is the Secure Access Service Edge (SASE). SASE combines network security functions with WAN capabilities to support the dynamic, secure access needs of modern organizations. Imagine it as a security checkpoint that ensures only authorized users and devices can access your network, no matter where they are. This approach is crucial for businesses with remote workers or multiple locations, as it provides consistent security across all access points.
By integrating these cutting-edge technologies, organizations can achieve a secure and reliable cloud environment. This not only protects sensitive information but also ensures that businesses can operate smoothly and efficiently in the digital world.
As companies continue to accept the cloud, these innovations in cloud security and connectivity will play a vital role in safeguarding their operations and data.
Frequently Asked Questions about Cutting-Edge Security Technology
What is cutting-edge technology in cybersecurity?
Cutting-edge technology in cybersecurity refers to advanced tools and systems designed to protect digital assets from cyber threats. These technologies include artificial intelligence (AI), quantum computing, and blockchain, among others. They help organizations stay ahead of cybercriminals by providing innovative solutions for threat detection, data protection, and network security.
What are the top cutting-edge technologies right now?
Several technologies are leading the way in cybersecurity:
-
Artificial Intelligence (AI): AI-driven solutions are changing cybersecurity by offering real-time threat detection and automated responses. These systems can analyze vast amounts of data quickly, identifying potential threats before they cause harm.
-
Quantum Computing: This emerging technology promises to revolutionize data encryption, making it more secure and resistant to cyberattacks. Quantum-resistant encryption algorithms are being developed to protect sensitive information against future threats posed by quantum computers.
-
Biotechnology: While primarily associated with healthcare, biotechnology is making its way into security. For example, biometric authentication methods, such as fingerprint and facial recognition, are becoming more sophisticated, providing improved security for accessing digital assets.
How does cutting-edge technology improve security?
Cutting-edge technology improves security through a multi-layered approach that combines advanced tools and strategies:
-
AI and Automation: By automating threat detection and response, AI reduces the time it takes to identify and mitigate cyber threats, minimizing potential damage.
-
Innovative Solutions: Technologies like blockchain provide secure transaction methods, ensuring data integrity and reducing the risk of fraud.
-
Quantum Security: As quantum computing evolves, its potential to break traditional encryption methods is countered by developing quantum-resistant algorithms, safeguarding sensitive data.
These technologies work together to create a robust security framework, protecting digital assets from increasingly sophisticated cyber threats. By staying informed and adopting these innovations, organizations can improve their cybersecurity posture and ensure their data remains secure in an changing digital landscape.
Conclusion
American S.E.A.L. Patrol Division stands at the forefront of security services in Texas, leveraging cutting-edge security technology to ensure unparalleled protection for both residential and commercial properties. With over 15 years of experience, we pride ourselves on combining state-of-the-art technology with the expertise of our highly trained personnel to deliver 24/7 monitoring and rapid response.
Our commitment to safety and peace of mind is unwavering. We understand that in today’s world, security needs are constantly evolving. That’s why we continuously invest in the latest technologies and training for our team. Whether it’s through advanced surveillance systems, AI-driven threat detection, or cloud-based security solutions, we ensure that our clients receive the most effective protection available.
Our expert personnel are the backbone of our operations. Equipped with the latest communication tools and trained in both armed and unarmed security measures, they are prepared to handle any situation with professionalism and efficiency. Their dedication to maintaining a safe environment is evident in everything they do, from conducting regular patrols to providing exceptional customer service.
By choosing American S.E.A.L. Patrol Division, you are investing in a security partner that prioritizes your safety through a multi-layered approach. We are here to protect what matters most to you, allowing you to focus on your core activities without security concerns.
For more information on how we can improve your security, visit our security services page. Join us in building a safer tomorrow with our comprehensive and innovative security solutions.